PAM for Cybersecurity: Strengths, Flaws, and a Better Approach
Cyber-attack news is so common nowadays that they’re almost not newsworthy anymore. According to Cybersecurity Ventures, cybercrime will cost the world $10.5 trillion annually by 2025, up from $3 trillion in 2015. To put this into perspective, cybercrime will be the world’s 3rd largest economy if measured as a country, after USA and China.
Despite the growth in cybercrimes, many businesses still overlook the importance of cybersecurity.
For companies looking to build cybersecurity resilience, adopting a Privileged Access Management (PAM) tool is a great way to start. However, it is important to note that PAM is just one building block for cybersecurity, and achieving cybersecurity resilience requires a layered approach.
Then, how does PAM fit into cybersecurity? What are its strengths and weaknesses when it comes to cybersecurity?
TABLE OF CONTENTS
STRENGTHS: How PAM should Improve Cybersecurity
FLAWS: Common Shortcomings of PAM for Cybersecurity
How Hackers are Still Successfully Compromising Privileged Accounts
No Cost, Big Protection.
Download Mamori Freemium and begin securing your jump servers with Mamori.io’s free, easy-to-use solution.
The Goal of PAM
Privileged Access Management (PAM) is a tool that companies deploy to protect sensitive and confidential data and assets. It ensures that ONLY privileged users, such as administrators, have access to those sensitive data. Meanwhile, PAM enables the enforcement of least-privilege access policy – where users only have access to the data and resource they need to perform their duties. This boosts cybersecurity and protects against internal breaches as well.
STRENGTHS: How PAM Should Improve Cybersecurity
Although different PAM solutions have different approaches, they should all be able to protect against cybersecurity in the following ways, at the minimum:
Reduce Attack Surface and Damage
A cybercriminal’s attack surface is greatly reduced when the majority of employees, processes and apps don’t have access to the sensitive data sought by criminals. A compromised laptop used by an entry-level employee will have little value to a cybercriminal, and the damage will only be limited to what data the entry-level employee had access to. With PAM, attackers must go after privileged accounts if they want to score big.
Password Protection
Even when an attacker manages to gain access to a machine, password vaulting adds another layer of security by storing usernames and passwords of privileged accounts in a secure, encrypted format. Some PAM solutions include password generation and rotation as well as credential approval systems. This means that even if an attacker manages to steal privileged credentials, they only have a limited timespan to access the compromised privileged account.
Track & Monitor Privileged Activity
Most PAM solutions monitor and log all privileged access and activities for audit and compliance requirements. This monitoring and tracking feature is another feature that boosts cybersecurity, which helps identify access anomalies or sudden privilege escalations. The logs history can uncover suspicious activities, such as a privileged SSH session at 3am from a foreign country. More advanced solutions, such as what Mamori.io provides, takes it to the next level by identifying anomalies based on database access and operation, such as unusual database queries or mass data export or deletion.
FLAWS: Common Shortcomings of PAM for Cybersecurity
Some of the most notable security breaches occurred because of privileged access abuse or mismanagement. A few examples include Yahoo!, U.S. Office of Personnel Management, and Uber. That is why, as noted earlier, PAM is just one building block to achieve cybersecurity resilience.
Moreover, PAM solutions are complex and time-consuming to manage, often creating additional cybersecurity risks.
Creating and maintaining privileged accounts following the ISO 27001 process can be cumbersome, which requires provisioning (VPN, RDP, SSH, database authorization) and account validity checks with monthly reports and email follow-ups from admins to those requesting privileged access. To save from these tedious tasks, some admins opt for insecure ways of managing privileged accounts, as mentioned below, which effectively creates additional opportunities for cybercriminals to exploit and use to plan an attack.
Over-Provisioning Access
To save time and trouble, organizations tend to over-provision access – “get it all in the initial ask” – instead of “get just what’s needed when you need it”. This is understandable because over-provisioning access increases administrator’s work productivity, and workflows won’t be disrupted because of insufficient access. The accounts with excessive access are what increases the attack surface for cybercriminals.
Unused, Forgotten & "Zombie" Accounts
For most PAM solutions, offboarding privileged accounts is a manual (and sometimes laborious) process. If admins are not constantly following up with users, newly created accounts are usually forgotten. Employees who were promoted or switched roles would still have access to systems they don’t need. Employees who left the company may still have access. All of these present considerable risks and increase the attack surface of a cyberattack.
Password Sharing
Passwords sharing is what some admins do when they’re just too busy. When passwords are shared, they are usually stored somewhere insecure, like spreadsheets or other files on desktops. Further, shared passwords are usually easy-to-guess, which increases the vulnerability of a brute force cyber-attack. Password sharing also makes it difficult to audit privileged accounts should an incident arise.
Not Updating Default Credentials
By default, some accounts have privileged access by default. Those default credentials are common knowledge and are primary targets for cybercriminals. Even so, some organizations do not rotate or update these credentials because it can be time-consuming, error prone, or intensive in some cases.
Lack of Monitoring & Oversight
The lack of monitoring and account oversight is the primary cause of forgotten & zombie accounts. Worse, when a forgotten account suddenly becomes active because of stolen credentials, nobody would notice because of the lack of monitoring. As a result, suspicious activities cannot be identified in-time, and security incidents cannot be properly mitigated.
Complexities in Deployment
Because of deployment complexities, most organizations deploy PAM only on the operating system. They purposely neglect deploying on other layers, such as Active Directory and databases, because most organizations deploy PAM for compliance and not for data security. This failure to fully deploy PAM is what prevents PAM from fully achieving its data security potential. But even when PAM is fully deployed, it still has the shortcomings mentioned above.
How Hackers are Still Successfully Compromising Privileged Accounts
Forrester estimates that 80% of data breaches are directly or indirectly connected to compromised privileged accounts. Because of the above shortcomings and other vulnerabilities, hackers are still able to compromise privileged accounts. Below is a short summary of that process:
Step 1: Compromise a Local Account
IT admins with privileged accounts are (typically) extra cautious. Unless the admin is targeted by a sophisticated, well-designed social engineering attack, the admin’s credentials are not easily compromised. However, it is a different story for other employees. To compromise a local account, hackers typically deploy phishing scams, drive-by downloads or fake-websites to get malware installed in an employee’s local machine.
Step 2: Explore IT Environment While Remain Hidden
Once the malware-infected machine connects to the company’s network, the cyber criminal now has access to explore the company’s IT environment disguised as an authorized user (also commonly known as Man in the Middle or Pass the Hash attacks). The key here is to stay hidden so the cyber criminal can observe and record operational routines. At the same time, they can install remote access kits or key loggers to seek out passwords, SSH keys, and other credentials so they can escalate access if they don’t already have them.
Step 3: Steal Passwords or Escalate Privileges
Their reconnaissance mission from Step 2 will uncover system vulnerabilities, such as unpatched servers, default credentials, shared passwords (sometimes stored on desktop, spreadsheets), and unused zombie accounts, all of which gives them privileged access. If no privileged accounts were compromised, some cyber criminals may blatantly request for escalated privileges as the compromised user. The request will be approved if IT admins routinely over-provision access.
A BETTER APPROACH: PAM for Cybersecurity by Mamori.io
The problem with most PAM solutions is that they are complex, manual, and time-consuming to use. Admins who are short on time would circum-navigate this by deploying risky practices that increases cybersecurity vulnerabilities, such as over-provisioning access and those mentioned earlier.
Instead of all the complex and manual processes, Mamori.io took a different approach that not increases cybersecurity resilience, but also saves admins more than 90% of their time and effort when managing privileged access.
Instead of putting all the workload on admins, Mamori.io requires the users to ask for the type of access needed, pending the approval of admins. Then, account validity checks are automated or on-demand, and access terminations are automated based on pre-set security policies.
Key benefits of this approach include:
· Eliminating unknown or unmanaged privileged accounts
· Activity monitoring and automated alerts of suspicious activity
· Increased productivity and reduced workload for admins
· Eliminating “too much access” and implementing least privilege access
· Streamlined workflow without disruptions
Below is how Mamor.io’s PAM (M4PAM) compares:
To reiterate, the root cause of cybersecurity risks of traditional PAM solutions is the hefty workload on the admin. With M4PAM, the whole ISO 27001 process, including creating and managing privileged accounts, are automated as shown below:
Mamori.io’s approach to PAM removes the shortcomings and cybersecurity risks of traditional PAM solutions. Here’s how Omar Masri, our founder and CEO, puts it:
“It is comprehensive security solutions, not security features, that protect businesses from hackers and data theft and loss. Mamori.io is a comprehensive solution. A PAM product are just security features. For businesses that deploy PAM for compliance, they might as well deploy Mamori.io instead. We have all the compliance features AND it comes with ransomware and data loss protection.”
-Omar Masri, Founder and CEO of Mamori.io
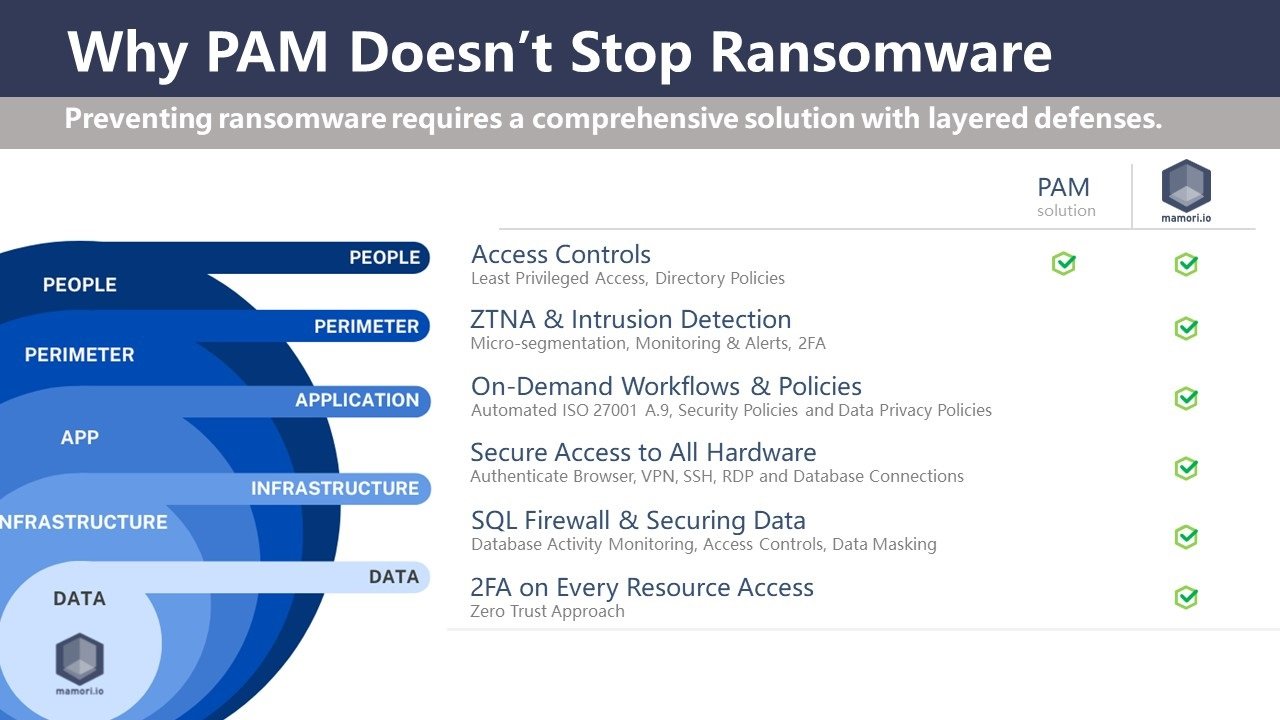
Cybersecurity Requires a Layered Approach
PAM is just one layer of security for those looking to achieve cybersecurity resilience. As noted in our Ransomware Prevention Best Practices: A Layered Approach, successfully defending against cyber threats requires multiple layers – from the endpoint to the network and all the way to databases and backups.
Mamori.io provides multiple layers of security, including PAM, Intrusion Detection, Database Activity Monitoring, Zero Trust Network Access (ZTNA) and more. In essence, if you have a firewall and endpoint security, Mamori.io is the only solution you’ll need to achieve cybersecurity resilience.
For businesses that lack the budget and time to build cybersecurity, we offer managed cybersecurity services with advanced layers of security, at a fraction of the cost, and with no effort on your part. We can help deploy our all-in-one cybersecurity solution on your infrastructure (self-hosted) or on our infrastructure (as a managed service). This is ideal for businesses who don’t have the expertise, resources or time to deal with all the cybersecurity complexities, such as implementation, maintenance, and monitoring.
If you’re a small business concerned with cybersecurity cost, deployment and maintenance, Mamori.io is your best option. Get started by requesting your free license today, or get started with our free PAM solution for small businesses.