Ransomware Protection and Prevention Solution
Ransomware hackers are after your files in shared drives and your data in databases. We secure them using a zero-trust network access model.
Preventing Ransomware Starts with Securing the RIGHT Things
Contrary to popular belief, ransomware hackers attack networks and databases, NOT applications. This means securing your applications logins with two factor authentication (2FA) or other means do NOT stop them. To stop ransomware hackers, you need to secure the file shares, databases and data that your applications and users have access to.
Mamori is the ONLY solution that integrates ALL the necessary security controls to secure your network files and databases from ransomware.
How Mamori Stops Ransomware Attacks
Securing Access
One stolen password took down the Colonial Pipeline, and compromised remote desktop protocol connections (RDP) were the most common attack vector in Q1 of 2021 (Coveware). You need to have the same level of security for all access to file shares, databases and data, whether local or remote.
Device Registration – Define which devices are allowed to access what kind of resources.
Two Factor Authentication (2FA) – Secure a person’s credentials using Mamori’s built-in 2FA or by integrating with your existing 2FA providers.
Access Controls by IP/Netmask – Only allow access by IP, netmask or a combination of all using Single Sign-On (SSO).
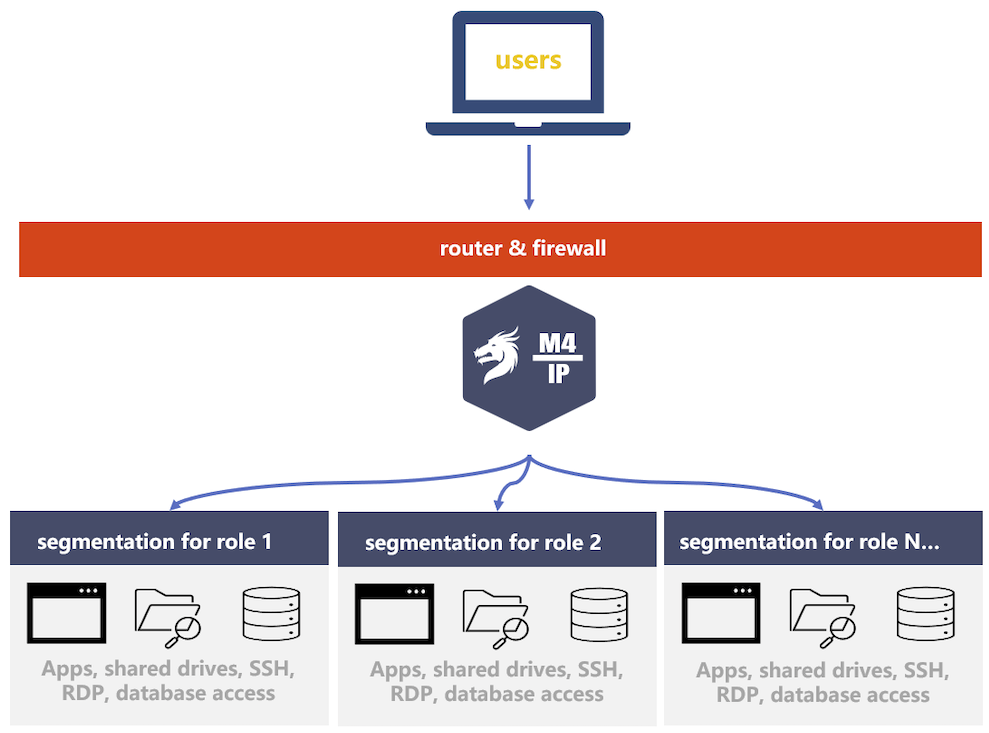
Micro-Segmenting Networks
Micro-segmentation involves splitting a larger network into smaller network segments, which protects against lateral movement on your network by ransomware hackers. A common practice is to segment more vulnerable networks so even when that network is compromised, other networks are protected.
Segment Based on Roles – It is common to segment a network for third parties or more vulnerable parts of the network.
Segment Based on Identity Workload – Networks that require more bandwidth should be segmented for faster and easier monitoring.
Secure Network Connection – Access to different networks can be provisioned with configurable Open VPN and SSH tunnels.
Detecting and Blocking Intrusions
Ransomware hackers scan for open ports to scope out the target environment to find vulnerabilities. Mamori effectively detects and blocks any unauthorized access and actions and notifies relevant users of such activities.
Network Access Identity – Network access can be identified as authorized or unsolicited, based on the device’s identity and permission levels.
Prevent Network Scans – Unsolicited attempts of a network scan will be automatically detected and blocked.
Access Notifications – Admins and owners of the compromised device and will be notified immediately of unauthorized use.
Securing Data
Even when a ransomware hacker is at the doorsteps of your data, their efforts can still be thwarted because their access is unauthorized. Mamori allows you to set controls on the data level, so access to sensitive information will be blocked or masked, rendering them useless to cybercriminals. Any unauthorized database operations will also be blocked.
Control Database Operations – Restrict the ability to run SQL or database commands based on level of access or preset table rules.
Masking & Obfuscating Data – Sensitive data can be masked, making them little to no value to unauthorized access.
Control Tables, Rows & Columns – Limit access to each database tables with multiple rules, including what rows and columns they have access to.
Monitoring, Alerting and Recording
Ransomware hackers need time to scope out and carry out their attacks. With Mamori’s monitoring, alerting and recording, any attack attempt can be easily identified and recorded by activity monitoring, with the users and admins notified of such activity.
Monitor Connections & Activity – Database connection sessions and their activities are monitored for anomalies.
Instant Alerts on Activities – Define the types of activities you want to be notified.
Session Recording – Direct database accesses and sessions are automatically recorded.
Protect Your Data from Ransomware in 3 Simple Steps:
Deploy a Mamori Server – Install Mamori in one of your servers, whether on-premise or cloud. No agents. No changes to servers, directories, or databases required. Setup an admin account and configure 2FA and alert settings.
Integrate with Existing Directory or Create New Identities – Your existing directory and access settings can be easily rolled over.
Define Access Controls – After defining roles and identities, configure what these roles can access and what they can do with those data.
Start Securing Your Servers and Databases from Ransomware
Are you a small business?
Get Mamori’s free cybersecurity and privacy solution for small business.