Zero Trust Network Access Solution (ZTNA)
Enhance your data security with a solution that’s less complex, easier to manage, and with significant cost savings compared to legacy security models.
Why You Need Zero Trust Network Access (ZTNA)
Ransomware Protection and Prevention
Stop Network Penetration Attacks
Secure ALL Access, Whether Remote or Internal
Achieve Zero Trust Security Model with Mamori in 6 Steps
Zero trust security is being used as a buzzword. Simply adding two factor authentication (2FA) does NOT mean you have zero trust security.
To achieve a zero trust security model, you need to have zero trust network access (ZTNA) that enhances security on the individual and network layer to protect all your resources in your infrastructure. Strong authentication is required, and trust has to be earned every single time. This level of security level should be applied to all staff, whether internal or remote, who has access to the network.
Mamori is the ONLY solution that integrates all the security tools to provide a ZTNA solution that helps you achieve a zero trust security model. Our ZTNA solution is free for small businesses with 20 users or less.
1. Securing Devices
The first step is to secure all devices using device registry. Mamori allows you to manage and monitor all devices that are able to access your organization’s resources. Devices that can be secured include:
Desktops and Laptops
Mobile devices
Internet of Things (IoT)
Servers and Databases
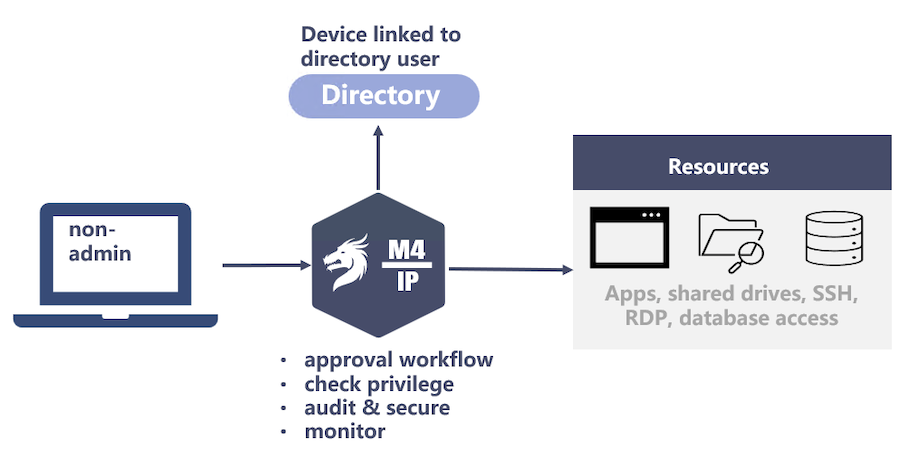
2. Securing Access by Identity & 2FA
In addition to securing devices, the users accessing the devices should also be secure using two factor authentication (2FA). The approach is to always verify the access to ensure the right person is behind the right device. The types of access that can be secured include:
Secure Shell (SSH)
Remote Desktop Protocol (RDP)
Direct Database Access
IP Address
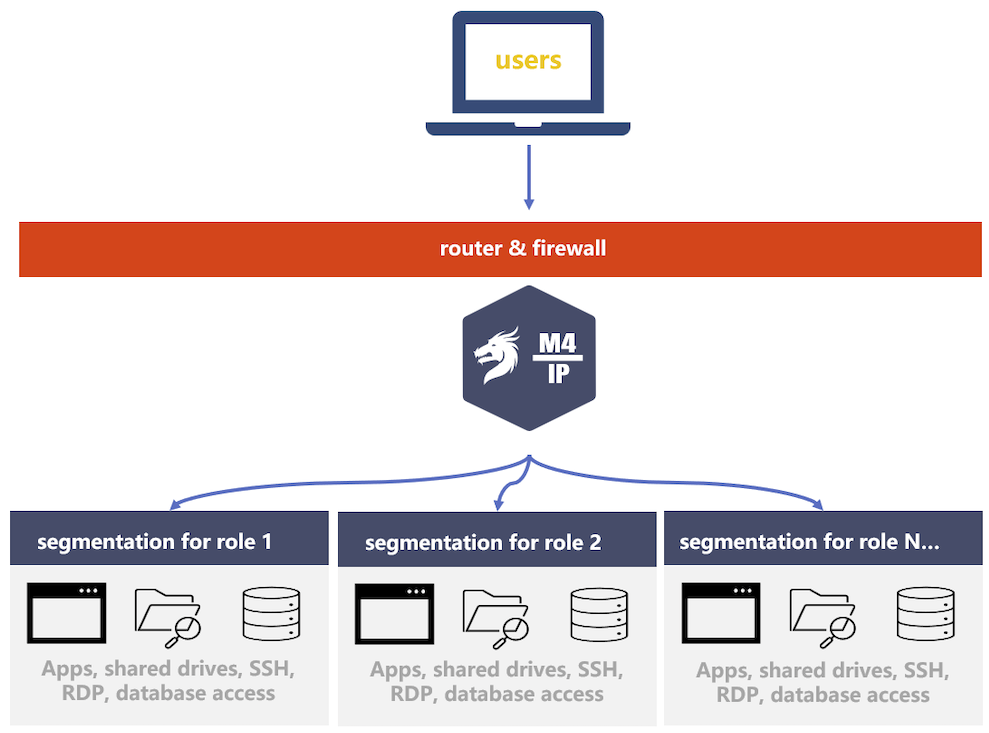
3. Micro-Segmenting Networks
Micro-segmentation splits a larger network into smaller network segments, which protects against lateral movement on your network by ransomware hackers. A common practice is to segment vulnerable networks or networks for third parties. With Mamori, networks can be further segmented based on:
Identity workload
Role-based workload
4. Implement Least Privileged Access
To implement least privilege, legacy security systems require you to select what access and resource to block, which is complex and difficult to manage. A zero-trust approach blocks everything and grants access based on the person’s identity or role, which is a simpler and more secure approach. Mamori allows you to define access rules such as:
Identity & role-based access
On-demand, as needed access
Database, data & application access
Data operation controls
5. Detecting and Blocking Intrusions
Every access and activity on the network should be identified and verified. Any unidentified network access, such as those by ransomware hackers, will be immediately identified. Their subsequent action, which is to scan the network to scope the environment, will be blocked, and relevant users will be notified. Mamori’s network intrusion detection features include:
Network access identity verification
Automatically block unsolicited network scans
Notifications for compromised access and activities
6. Monitor, Alert and Recording for Audit Reports
Any security solution is incomplete without analytics, logs and reporting. With Mamori, the entire lifecycle of any access session is logged and recorded. This includes who access the data, from what device, and what operations were completed in that session.
Security Analytics and Reports
Logs & Reports for each access
Recording & monitoring for each access
Session and activities monitoring & Alerts
Deploy ZTNA in 3 Simple Steps with No Network Changes:
Deploy a Mamori Server – Install Mamori in one of your servers, whether on-premise or cloud. No agents. No changes to servers, directories, or databases required. Setup an admin account and configure 2FA and alert settings.
Integrate with Existing Directory or Create New Identities – Your existing directory and access settings can be easily rolled over.
Define Access Controls – After defining roles and identities, configure what these roles can access and what they can do with those data.
Start Securing Your Business Data Using ZTNA
Are you a small business? Get our ZTNA solution for free (terms apply).